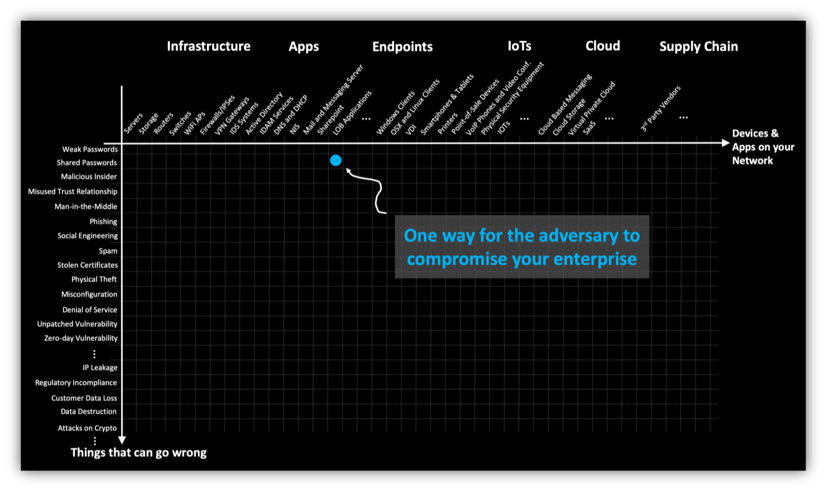
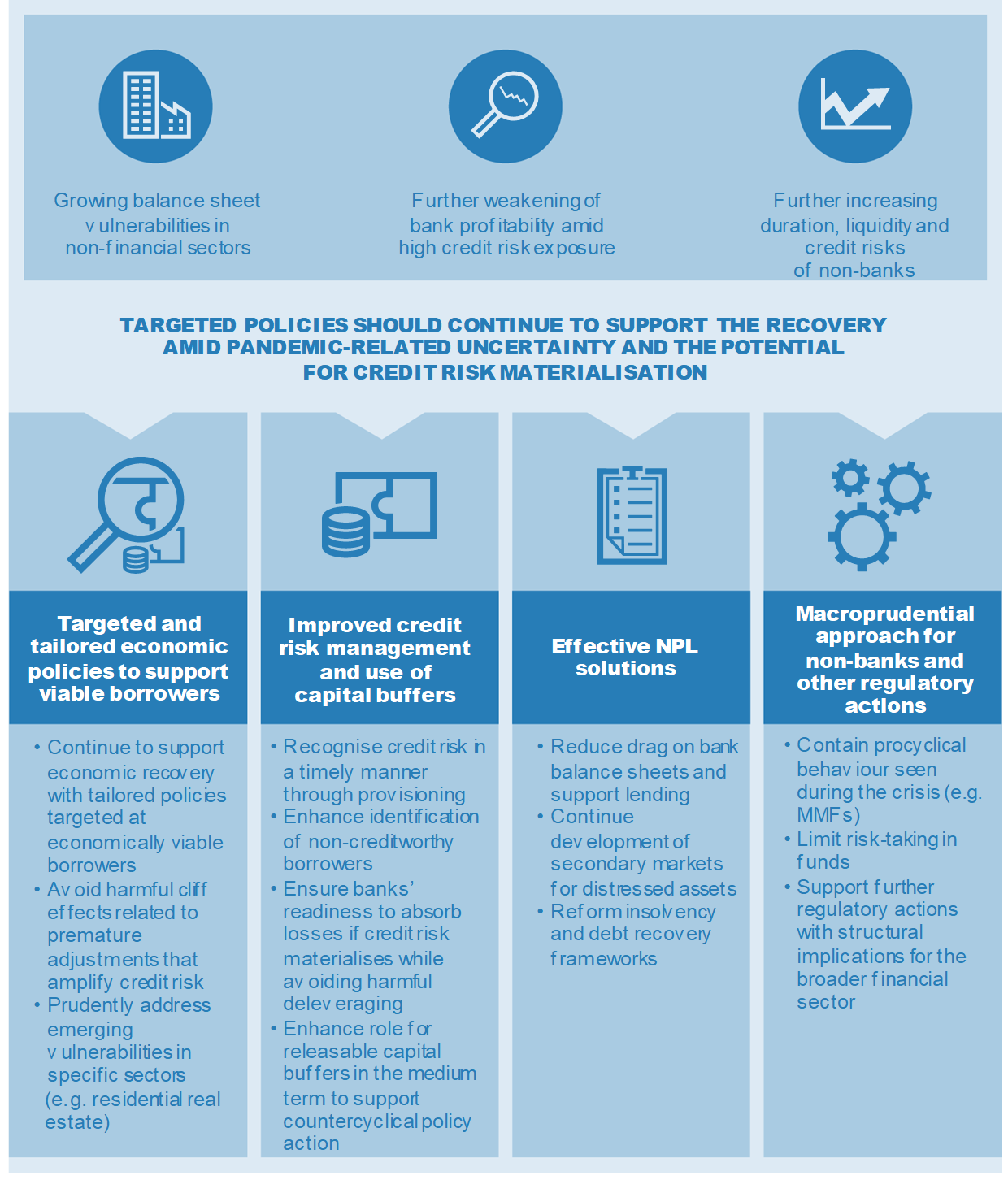
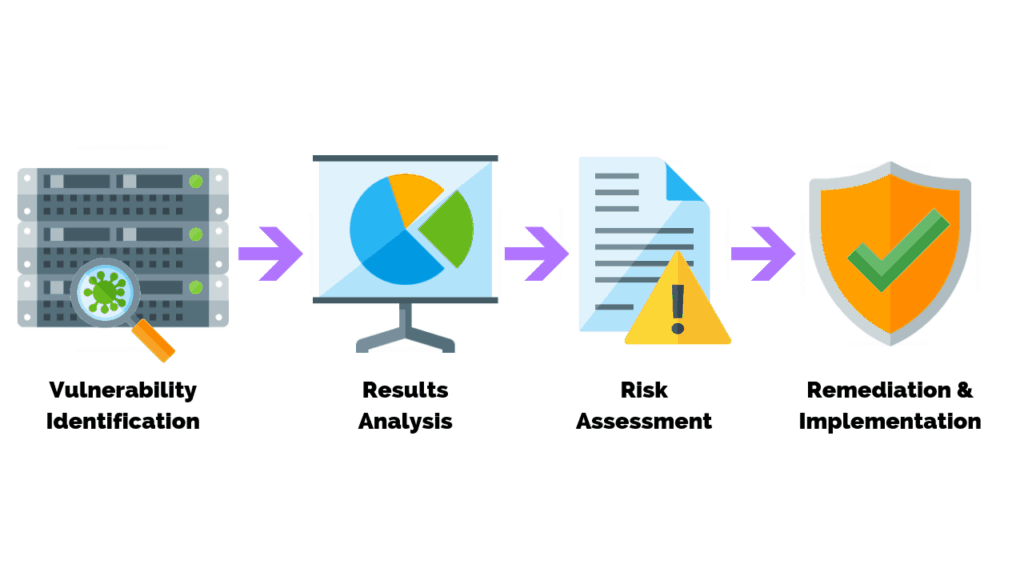
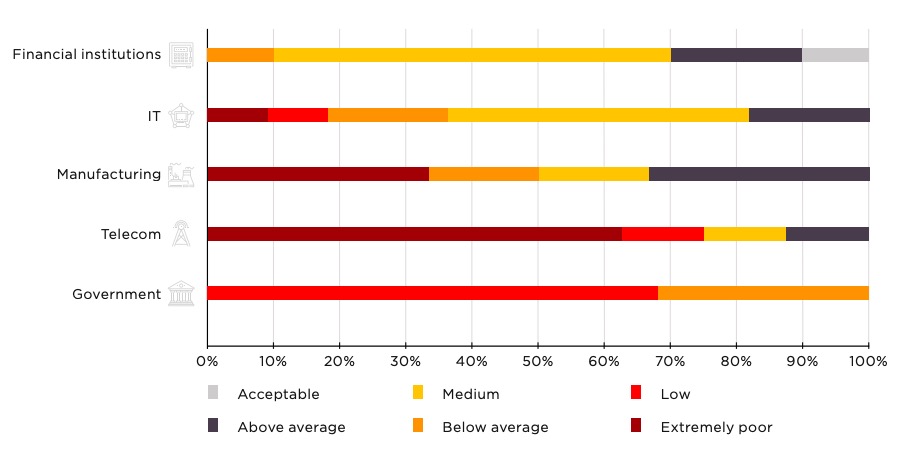
New Security Signals study shows firmware attacks on the rise; here's how Microsoft is working to help eliminate this entire class of threats | Microsoft Security Blog
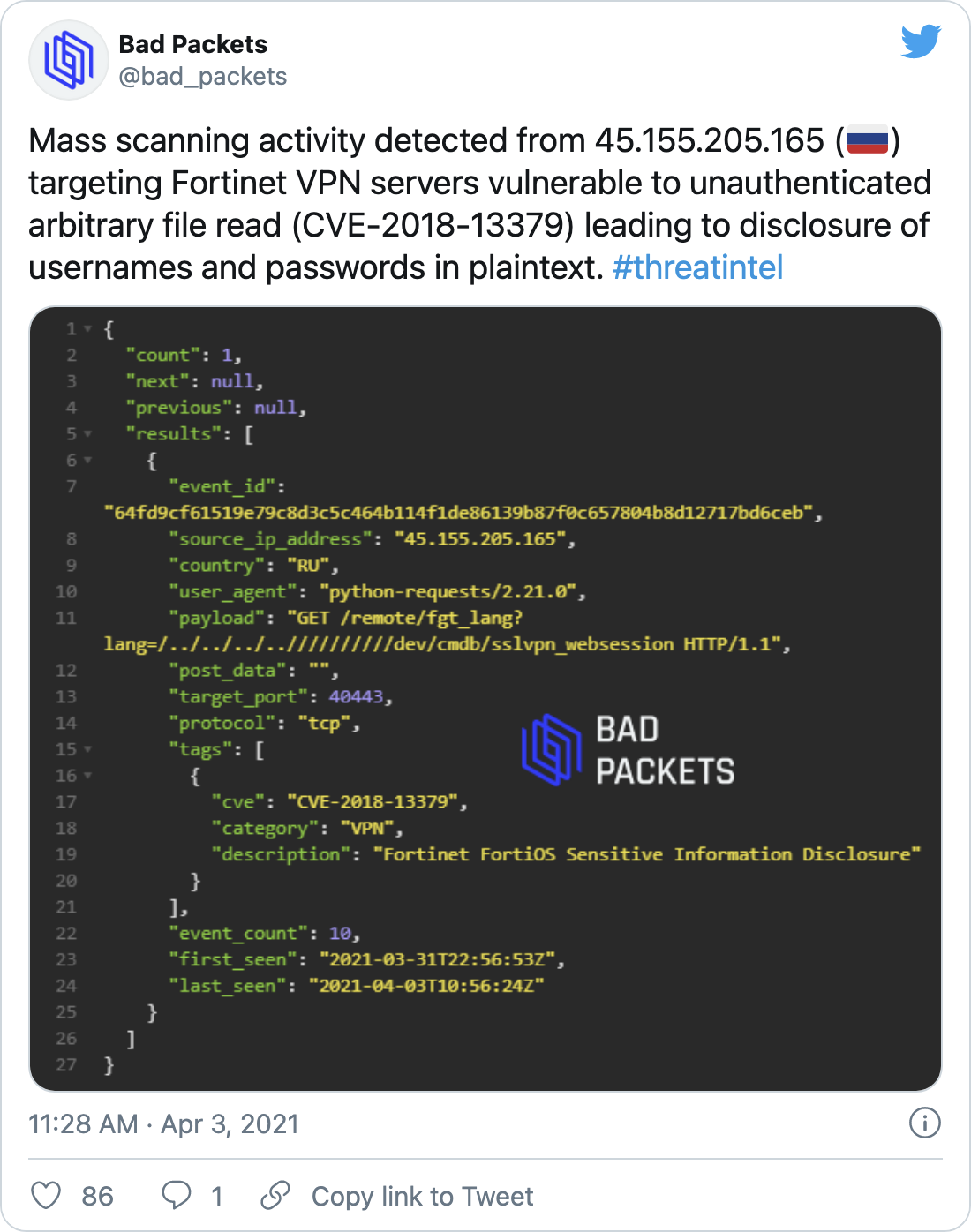
CVE-2018-13379, CVE-2019-5591, CVE-2020-12812: Fortinet Vulnerabilities Targeted by APT Actors - Blog | Tenable®

The Top 10 Most Exploited Vulnerabilities: Parsing an Important Recent National Cyber Awareness System Alert -- Security Today
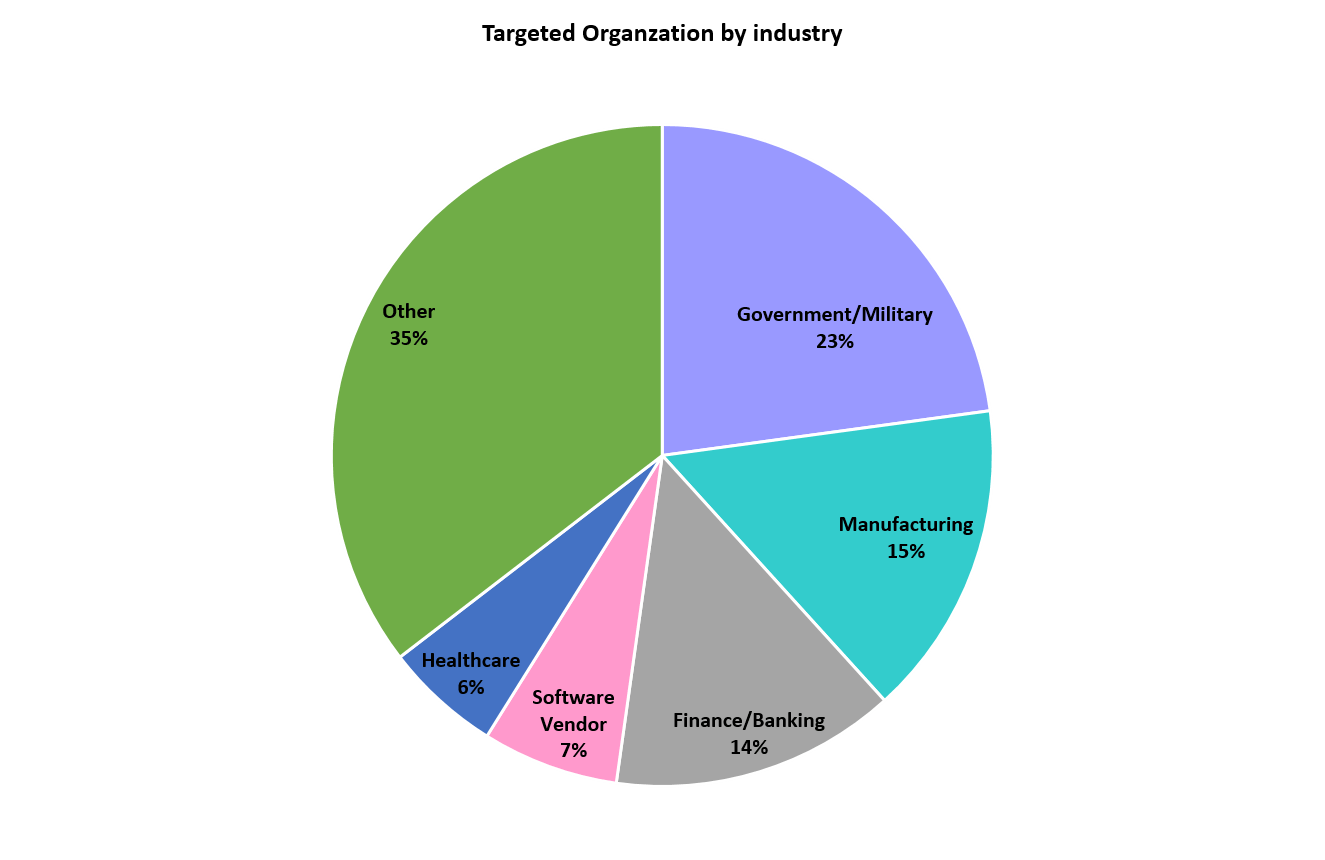
Exploits on Organizations Worldwide Grow Tenfold after Microsoft's Revelation of Four Zero-days - Check Point Software